In this digital economy, businesses have a single non-negotiable that determines their fate: security. The rising number and increasing sophistication of cyberattacks demand more than meeting the compliance minimum; online business owners need to be proactive to safeguard their customers and their ability to operate.
According to the FTC, global consumer losses in 2024 exceeded $12.5 billion, an increase of 25% compared to the previous year. Meanwhile, the threats to online businesses continue to grow, ranging from synthetic identity fraud and AI-assisted phishing attacks to vulnerable third-party software.
This guide outlines ten essential cybersecurity strategies for 2025 that every online business should implement to prevent fraud, ensure compliance, and build lasting customer trust.
1. Adopt AI-Powered Fraud Detection
Static fraud rules are history. And in 2025, online businesses are turning towards AI-enabled fraud detection methods to monitor transaction behaviours in real-time.
These systems observe and learn from consumer behavior and continually pick up new signals such as unprecedented buying patterns, mismatched IP locations, or suspicious device footprints. They reduce false positives and catch fraud attempts before they can do any damage.
Businesses are projected to spend over $10 billion by 2027 on AI-enabled financial fraud detection and prevention platforms, as per a study conducted by Juniper Research.
Pro Tip: Invest in payment platforms or plugins that leverage machine learning-based fraud prevention for dynamic and adaptive protection.
2. Stay Compliant with PCI DSS v4.0.1
The Payment Card Industry Data Security Standard (PCI DSS) has been updated to version 4.0, bringing more stringent regulations against emerging threats, followed by a new version 4.0.1 addressing minor revisions to 4.0.
For online business owners who process credit card transactions, the deadline to comply with the requirements is March 31, 2025.
While there are 12 core requirements, some of them are as follows:
- Protecting against malware
- Logging and monitoring access
- Protecting stored and transmitted cardholder data
- Multi-factor authentication
Next Step: Perform a compliance audit and work with a PCI-compliant payment processor to understand ways to improve and strengthen your security.
3. Require Multi-Factor Authentication (MFA)
Password breaches still represent one of the most frequently used attack techniques. MFA serves as an added layer of defense, whether that’s SMS codes, authenticator apps, biometrics, or hardware keys. It prevents phishing and stops attackers who might have access to passports and valid credentials.
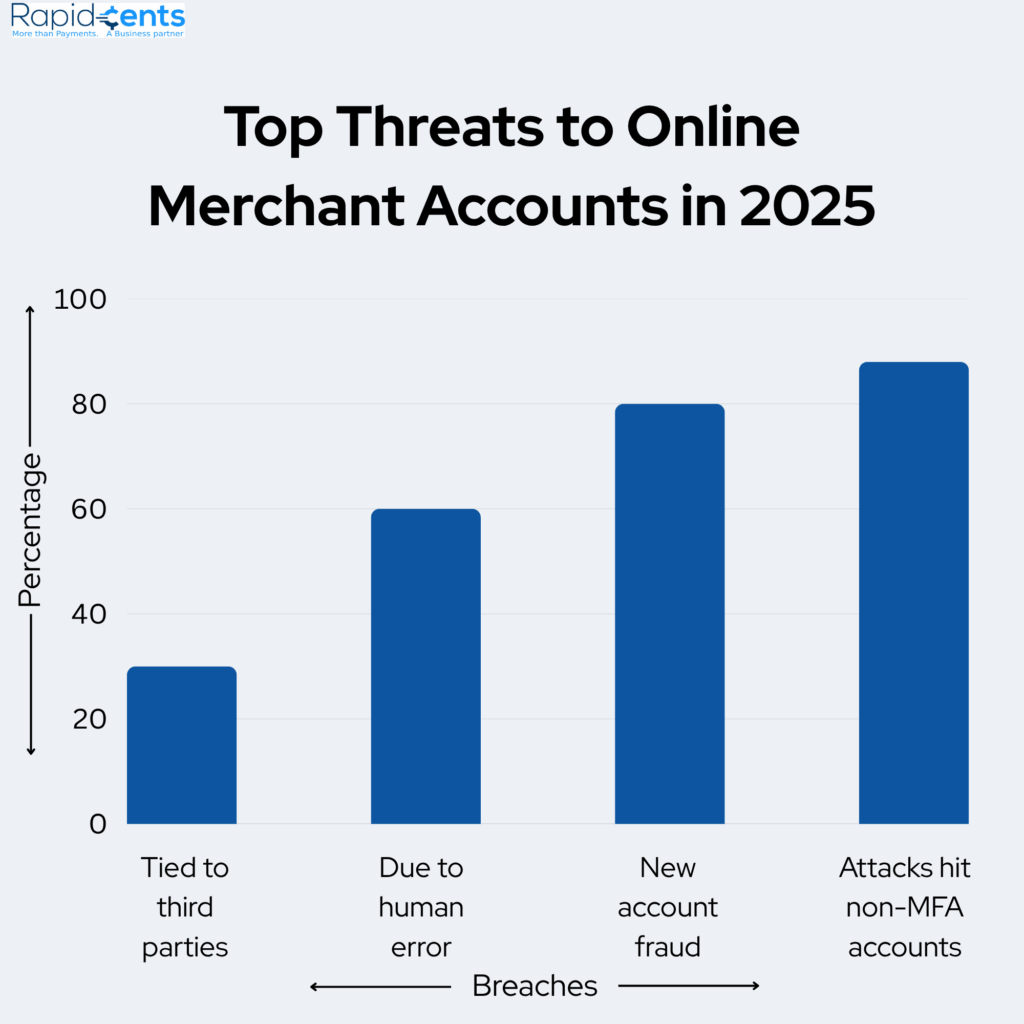
MFA protects against 88% of ransomware attacks that happen in accounts without MFA1 .
Bonus Tip: Utilize MFA not just for admin logins, but also for customer accounts and internal tools such as CRM and email platforms.
4. Detect Synthetic Identity Fraud Early
With the rise of AI, criminals are now turning towards AI-generated identities to create fake customer profiles and commit multiple frauds in other people’s names. This makes the traditional method of fraud detection ineffective.
As per a report by Experian, 80% of new account frauds are linked to synthetic ID fraud. The fake ID is first used to open accounts, build credit history, and then apply for loans or big money transactions in another person’s name.
Such frauds can lead to huge revenue losses for businesses.
What to Do: Advanced verification solutions can help assess behavioral data, device intelligence, and network signals to counter such schemes.
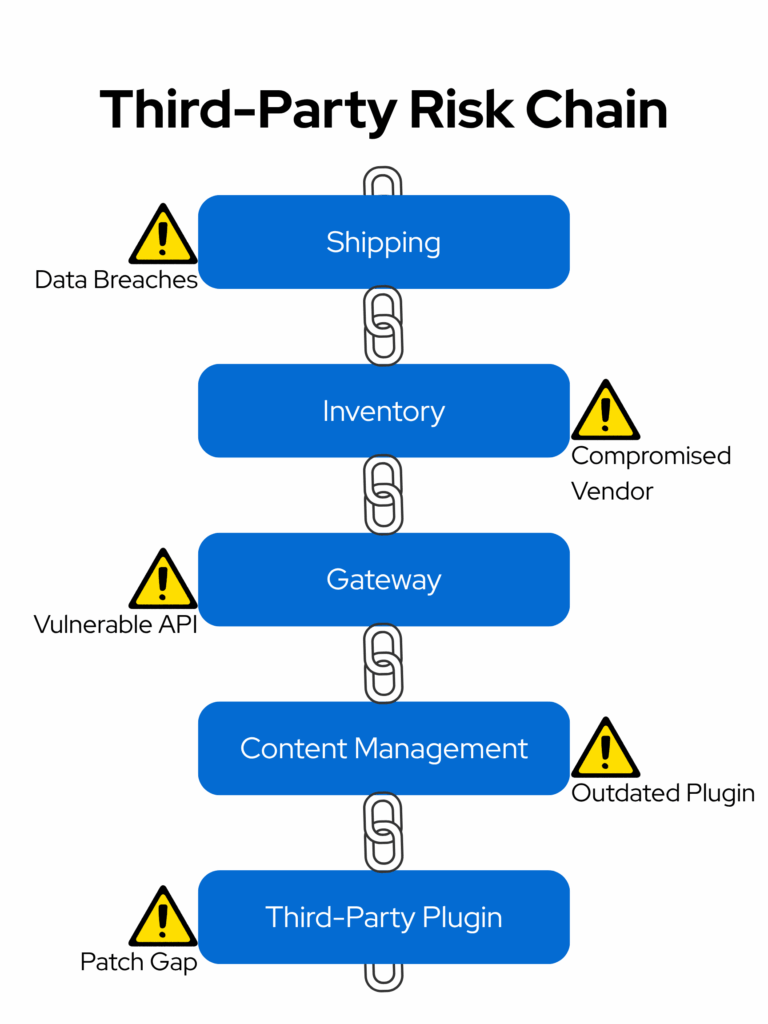
5. Audit Your Supply Chain and Integrations
Most modern online businesses rely on third-party integrations, platforms, and software to manage inventories, process payments, and ship products. Each external connection introduces a whole new list of vulnerabilities that can impact the entire business operations.
Risks that can be introduced through third-party integrations include:
- Compromised software
- Ransomware attacks
- Data breaches
According to Verizon’s 2025 DBIR, 30% of data breaches were linked to third-party involvement that exploited vulnerabilities and business disruptions.
Recommended Practice: Thoroughly vet vendors and platforms. Regularly perform reviews of all the integrations and remove unnecessary apps, API keys, and create a compliance system that all parties must follow.
6. Train Your Team to Recognize Social Engineering Attacks
Scammers are leveraging AI to create sophisticated phishing emails and messages that are able to impersonate legitimate people or businesses. Unspuspecting staff members can often end up clicking on links that allow attackers access to the business and lead to financial and reputational damages.
Verizon’s 2025 DIBR also highlighted that 60% of cybersecurity breaches involved a human element and were a result of phishing.
How to Act: Start a periodic security training program with phishing simulations and real-world breach examples.
7. Update and Patch All Software Regularly
Running outdated software exposes vulnerabilities. And while most businesses focus on sophisticated scams such as phishing, such vulnerabilities are an easier path for scammers to access the systems.
60% of breaches are a result of vulnerabilities with known patches that were readily available2.
Routine Tip: Enable automatic updates for CMS platforms and plugins. Schedule manual patching during low-traffic hours.
8. Implement Real-Time Transaction Monitoring
Real-time analytics helps identify and catch fraud as it is happening instead of waiting until after the transaction is complete. Businesses assign a fraud score to each transaction, and those with a higher score than the threshold are flagged immediately.
Some metrics used are flagging high-volume purchases, suspicious geolocations, or rapid-fire order attempts.
Enable It: Businesses can use AI-based tools to assign scores to transactions and receive live alerts about any fraud attempts.
9. Stay Informed on New Threats and Industry Changes
Cybersecurity is constantly evolving, and so are the scammers, looking to find new loopholes to exploit the system. For businesses to protect themselves from data or financial losses, it is important to stay updated on any changes within the industry.
Resources to Follow:
- PCI Security Standards Council (PCI SSC)
- Cybersecurity & Infrastructure Security Agency (CISA)
- Reputable blogs like Krebs on Security
Action Step: A team member can be assigned to constantly monitor the top sources for the latest updates or use AI-based tools to monitor threats and vulnerabilities and counter them.
Final Words: Security Is a Growth Enabler
Spending on cybersecurity is a form of insurance, but it’s also a tool to build trust, lower risks, and safely scale. Online businesses that adopt these strategies will secure operations, meet industry requirements, and advance their brand in 2025 and beyond.
By using common-sense compliance approaches, AI-powered tools, and a prepared workforce, business owners not only minimize the chance of a cyber-attack but also increase confidence in the eyes of their customers and guarantee long-term operational resilience.
Learn how RapidCents protects your payments from fraud and chargeback, reducing the risk of revenue loss at checkout.




